This is my walkthrough on the tryhackme soc level 1 starting at the pyramid of pain. This first section is hash values, what we learn is m5 and sha-1 have been phased out due to them being susceptible to either hash collisions (were two different files have the same hash) or the hash could be brute forced. SHA-2 is used currently the most common variation being SHA-256 which has a hash value of 256-bits as a 64 digit hexadecimal number.
Next we are given some screenshots of VirusTotal and OPSWAT which are hash lookup tools that can inform the user if the file is malicious. The problem with hashes is they can be changed by flipping a single bit. There is a type of malware known as refactoring malware this can rewrite parts of the virus as it spreads causing the files hash to change which makes it harder to detect.
Anyway towards the end we are given a screenshot of a PowerShell console that shows how a hash can be changed while keeping the same file.
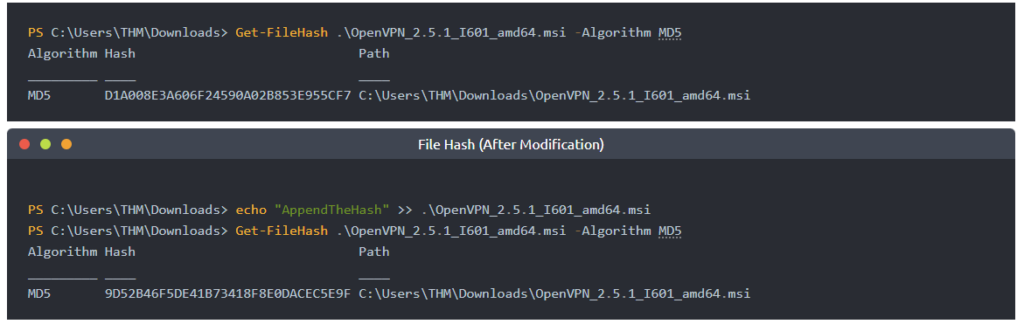
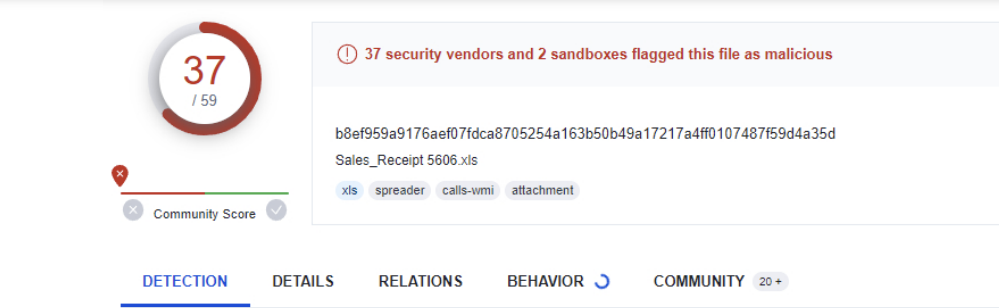
The question we are asked is the filename of the sample with the hash
“b8ef959a9176aef07fdca8705254a163b50b49a17217a4ff0107487f59d4a35d” the answer is
“Sales_Receipt 5606.xls”
As the hash is above the file name.
Leave a Reply